Automotive Cybersecurity: Protecting US Vehicles in 2026

The imperative for robust automotive cybersecurity US vehicles face by 2026 is critical, necessitating comprehensive strategies to safeguard connected and autonomous systems from escalating cyber threats, ensuring passenger safety and data integrity.
As vehicles become increasingly connected and autonomous, the need for stringent automotive cybersecurity US strategies has never been more urgent. By 2026, the US automotive landscape will face a new generation of sophisticated cyber threats, demanding innovative and proactive defense mechanisms. Understanding these evolving risks is paramount to safeguarding our transportation future.
The Evolving Threat Landscape for US Vehicles
The convergence of advanced driver-assistance systems (ADAS), infotainment, and vehicle-to-everything (V2X) communication transforms modern cars into highly complex, software-defined machines. This evolution, while offering unprecedented convenience and safety features, simultaneously expands the attack surface for malicious actors. The sheer volume of data exchanged and processed within and around vehicles presents fertile ground for cyber vulnerabilities.
Threat actors, ranging from opportunistic hackers to state-sponsored entities, are continuously refining their techniques. Their motivations vary, from data theft and intellectual property exploitation to vehicle hijacking and disruption of critical infrastructure. The potential for widespread chaos and economic damage underscores the gravity of these threats.
New Attack Vectors in Connected Cars
Connected vehicles introduce numerous entry points for cyberattacks, moving beyond traditional OBD-II port vulnerabilities. These new vectors leverage the vehicle’s extensive digital ecosystem.
- Remote Exploitation: Vulnerabilities in telematics units, infotainment systems, or cloud services can allow attackers to gain remote access to vehicle functions.
- Supply Chain Attacks: Compromised components or software within the automotive supply chain can introduce backdoors or weaknesses before vehicles even reach consumers.
- V2X Communication Interception: Weaknesses in vehicle-to-vehicle (V2V) or vehicle-to-infrastructure (V2I) communication protocols could enable eavesdropping, data manipulation, or denial-of-service attacks.
- Malware and Ransomware: Specialized malware designed for automotive embedded systems could disable functions, lock users out, or demand payment for restoration.
The continuous integration of new technologies, such as 5G connectivity and advanced AI for autonomous driving, further complicates the security posture. Each new feature, while beneficial, must be rigorously tested and secured from its inception to prevent future exploits. The industry must adopt a ‘security-by-design’ philosophy, embedding protective measures at every stage of development.
Current Cybersecurity Regulations and Standards in the US
Recognizing the escalating risks, US regulators and industry bodies are actively developing and implementing guidelines to bolster automotive cybersecurity. These efforts aim to create a standardized framework for security best practices, incident response, and continuous monitoring. The fragmented nature of regulations, however, presents a challenge for manufacturers operating across different jurisdictions.
Key initiatives focus on establishing a baseline for security requirements and promoting collaboration among stakeholders. This includes government agencies, automotive manufacturers, Tier 1 suppliers, and cybersecurity firms. The goal is to foster a collective defense against increasingly sophisticated threats.
NHTSA’s Role in Vehicle Cybersecurity
The National Highway Traffic Safety Administration (NHTSA) plays a pivotal role in ensuring vehicle safety, which now explicitly includes cybersecurity. NHTSA has issued guidance and best practices for securing connected vehicles, emphasizing a multi-layered approach.
- Cybersecurity Best Practices for the Safety of Modern Vehicles: This document outlines recommendations for manufacturers, focusing on product development, incident response, and organizational security.
- Information Sharing: NHTSA encourages the sharing of threat intelligence and vulnerabilities within the automotive industry to accelerate collective defense efforts.
- Regulatory Oversight: While not yet mandating specific technical standards, NHTSA’s guidance strongly influences industry practices and future regulatory directions, pushing for proactive security measures.
Beyond NHTSA, other bodies like the National Institute of Standards and Technology (NIST) provide cybersecurity frameworks that can be adapted for the automotive sector. These frameworks offer a structured approach to managing cybersecurity risks, identifying vulnerabilities, and implementing controls. The challenge lies in translating these broad guidelines into specific, enforceable technical requirements for vehicle manufacturers.
Emerging Technologies and Their Security Implications by 2026
The rapid advancement of automotive technology acts as a double-edged sword. While it promises enhanced safety, efficiency, and comfort, it also introduces novel cybersecurity challenges. By 2026, several key technologies will further redefine the threat landscape, demanding innovative security solutions.
These emerging technologies are not isolated; they interact in complex ways, creating intricate dependencies and potential points of failure. Understanding these interdependencies is crucial for developing holistic cybersecurity strategies that can withstand future attacks.
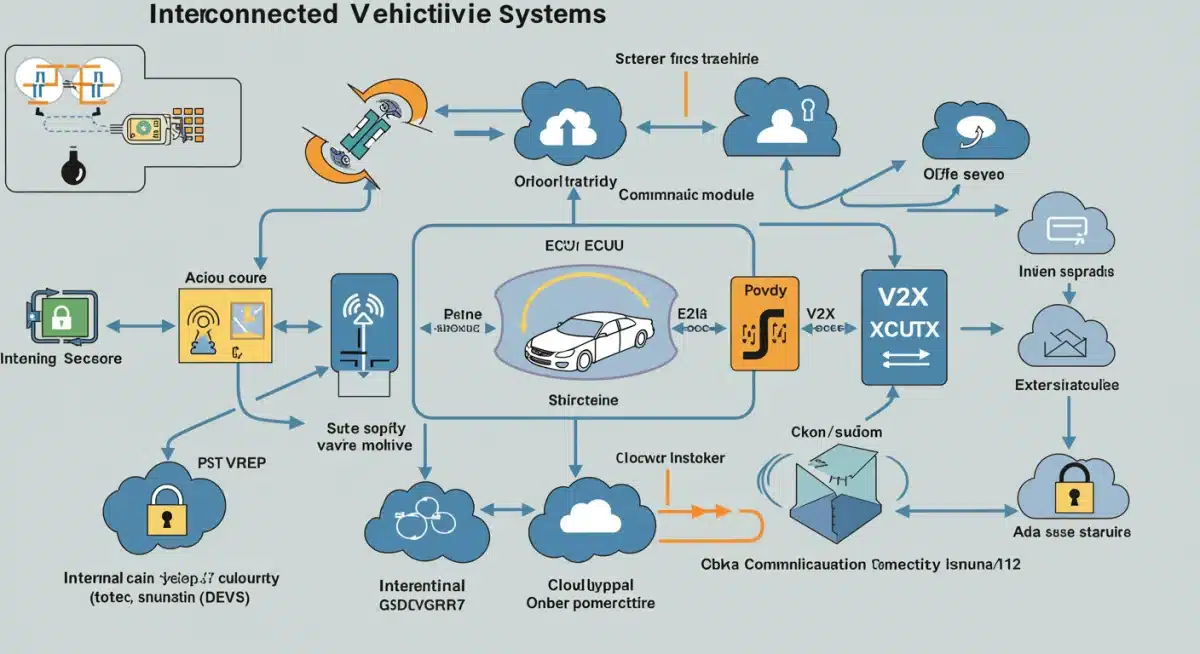
The integration of artificial intelligence and machine learning, for instance, offers powerful tools for intrusion detection but also presents new avenues for adversarial attacks against AI models themselves. Similarly, quantum computing, while still nascent, holds the potential to break current encryption standards, necessitating a shift towards quantum-resistant cryptography.
5G and V2X Communication Security
The rollout of 5G networks and the widespread adoption of V2X communication protocols are foundational to the future of connected and autonomous driving. However, these technologies introduce significant security considerations.
- Increased Bandwidth & Data: 5G’s high speed and low latency enable massive data exchange, making it a prime target for data interception or manipulation.
- Expanded Attack Surface: V2X communication, including V2V, V2I, V2P (vehicle-to-pedestrian), and V2N (vehicle-to-network), creates a vast network of interconnected nodes, each a potential vulnerability.
- Authentication and Integrity: Ensuring the authenticity and integrity of messages exchanged between vehicles and infrastructure is paramount to prevent false information or malicious commands from impacting vehicle operation.
The security of these communication channels requires robust encryption, secure authentication mechanisms, and real-time threat detection. Furthermore, the reliance on cloud infrastructure for processing and storing vehicle data necessitates strong cloud security protocols. Any compromise in these areas could have far-reaching consequences, affecting not only individual vehicles but entire transportation systems.
Proactive Defense Strategies for US Automotive Cybersecurity
To effectively counter the evolving cyber threats, the US automotive industry must adopt a proactive and multi-faceted approach to cybersecurity. This involves embracing a ‘security-by-design’ philosophy, investing in advanced threat intelligence, and fostering a culture of continuous improvement.
No single solution will suffice; instead, a layered defense strategy is essential, combining technological safeguards with robust processes and human expertise. Collaboration across the entire automotive ecosystem, from chip manufacturers to end-users, is critical for building resilient systems.
Implementing Security by Design and Default
Integrating security considerations from the earliest stages of vehicle development is fundamental. This means moving beyond reactive security measures to embedding protective features into hardware and software from the ground up.
- Secure Hardware Elements: Utilizing hardware-based security modules (HSMs) and trusted platform modules (TPMs) to protect cryptographic keys and ensure secure boot processes.
- Secure Software Development Lifecycle (SSDLC): Incorporating security reviews, threat modeling, and penetration testing throughout the software development process.
- Least Privilege Principle: Designing systems so that components and users only have the minimum necessary access rights to perform their functions, limiting the impact of a breach.
Furthermore, vehicles should be designed with ‘security by default,’ meaning that the most secure configurations are enabled out-of-the-box, without requiring users to manually activate them. This reduces the risk associated with user error or oversight. This proactive stance significantly raises the bar for attackers, making it much harder to find and exploit vulnerabilities.
The Role of AI and Machine Learning in Vehicle Security
Artificial intelligence (AI) and machine learning (ML) are becoming indispensable tools in the fight for automotive cybersecurity. Their ability to process vast amounts of data, identify patterns, and predict threats far surpasses human capabilities, offering a powerful advantage in detecting and responding to attacks in real-time.
However, the deployment of AI in security also introduces new challenges. Adversarial AI attacks, where machine learning models are tricked or manipulated, pose a growing concern. Therefore, securing the AI systems themselves is as crucial as using them for security.
AI-Powered Threat Detection and Response
AI algorithms can analyze vehicle network traffic, sensor data, and behavioral patterns to identify anomalies indicative of a cyberattack. This enables faster detection and automated response mechanisms.
- Intrusion Detection Systems (IDS): AI-driven IDSs can monitor in-vehicle networks for unusual activity, such as unauthorized access attempts or abnormal data flows.
- Predictive Analytics: ML models can analyze historical attack data and threat intelligence to predict potential future vulnerabilities and recommend preventative measures.
- Automated Incident Response: AI can facilitate rapid isolation of compromised components, deployment of patches, and even autonomous vehicle behavior adjustments to mitigate risks during an attack.
The continuous learning capabilities of AI systems mean that they can adapt to new and evolving threats, making them a dynamic defense mechanism. As attackers develop new methods, AI-powered security systems can learn from these new attack vectors and update their detection capabilities accordingly, providing a constantly improving shield for vehicles.
Collaboration and Information Sharing in the Automotive Industry
Given the global nature of cyber threats and the interconnectedness of the automotive supply chain, collaboration and information sharing are paramount. No single entity can effectively combat all threats in isolation. A unified front, sharing intelligence and best practices, strengthens the collective security posture of the entire industry.
This collaborative approach extends beyond direct competitors to include cybersecurity researchers, government agencies, and academic institutions. The goal is to create a robust ecosystem where vulnerabilities are quickly identified, shared responsibly, and patched efficiently.
Building a United Front Against Cyber Threats
Industry consortia and government-led initiatives are crucial for facilitating effective information exchange and developing common security standards.
- Automotive Information Sharing and Analysis Center (Auto-ISAC): This organization serves as a central hub for sharing and analyzing intelligence about cyber threats and vulnerabilities specific to the automotive industry.
- Standardization Bodies: Organizations like ISO and SAE are developing international standards for automotive cybersecurity management systems (e.g., ISO/SAE 21434), providing a common framework for manufacturers.
- Public-Private Partnerships: Collaboration between government agencies (e.g., DHS, FBI) and private industry helps in understanding emerging threats and coordinating national cybersecurity efforts.
By actively participating in these collaborative efforts, automotive manufacturers and suppliers can leverage shared knowledge and resources to enhance their individual security measures. This collective intelligence allows the industry to stay ahead of malicious actors, anticipate future attacks, and implement more resilient defense strategies across the board, ultimately benefiting consumers through safer and more secure vehicles.
| Key Aspect | Brief Description |
|---|---|
| Evolving Threats | Connected vehicles face sophisticated remote exploits, supply chain attacks, and V2X communication vulnerabilities. |
| Regulatory Landscape | NHTSA and other bodies provide guidance, pushing for ‘security-by-design’ and industry-wide best practices. |
| Proactive Defenses | Adopting security-by-design, secure hardware, and continuous software development lifecycle practices. |
| AI’s Role | AI and ML are crucial for real-time threat detection, predictive analytics, and automated incident response. |
Frequently Asked Questions About Automotive Cybersecurity
By 2026, primary threats include sophisticated remote exploitation of vehicle software, supply chain attacks on components, vulnerabilities in V2X communication, and the proliferation of specialized automotive malware and ransomware. These exploit the increasing connectivity and complexity of modern vehicles.
US regulations, primarily guided by NHTSA, focus on establishing best practices for vehicle cybersecurity, promoting information sharing, and influencing industry standards. While specific mandates are evolving, the emphasis is on ‘security-by-design’ and robust incident response frameworks to ensure safety.
5G’s high bandwidth and low latency enable massive data exchange for connected vehicles, expanding the attack surface. This necessitates robust encryption, secure authentication for V2X communications, and real-time threat detection to prevent data interception or malicious command injection, securing the future of mobility.
‘Security by design’ means integrating cybersecurity considerations from the very beginning of a vehicle’s development cycle. This includes using secure hardware, implementing a secure software development lifecycle, and adhering to the principle of least privilege, rather than adding security as an afterthought.
Collaboration is crucial because cyber threats are global and sophisticated. Information sharing through organizations like Auto-ISAC, public-private partnerships, and adherence to international standards help the industry collectively identify vulnerabilities, share threat intelligence, and develop unified, more resilient defense strategies against cyberattacks.
Conclusion
The journey towards a fully secure automotive future in the US is complex and dynamic, requiring continuous vigilance and adaptation. By 2026, the convergence of advanced vehicle technologies and increasingly sophisticated cyber threats will necessitate a robust, multi-layered approach to automotive cybersecurity US vehicles. Embracing security-by-design principles, leveraging the power of AI for threat detection, and fostering unprecedented collaboration across the industry are not merely options but imperatives. The collective commitment to these strategies will determine our ability to protect vehicles, safeguard personal data, and ensure the safety and reliability of the next generation of transportation systems.